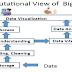
P2P overlay
network has a wide spectrum of communication frameworks in which peers build a
self-organized system that is fully distributed and cooperative. Figure 1
depicts the abstract P2P overlay architecture showing different components of
the overlay.
The Network
Communication layer describes the network characteristics of an end system/node
connected via internet, small wireless or sensor-based devices.
The Overlay
Nodes Management layer plays its part as management of peers which includes
discovery of peers and optimized routing algorithm.
The Features
Management layer deals with security, reliability, fault tolerance, and
robustness of P2P system.
The Service
Specific layer is to provide support to Application layer to utilize the
underlying resources in an efficient manner. It schedules the parallel and
computation-intensive tasks, and performs task like file management and
provides content. Here meta-data describes the information about content stored
across the peers and their location information.
The Application level layer describes the actual
functionality implemented over the underlying P2P overlay networks.
Structured
P2P:
In structured overlay network the network assigns keys to
data items and organizes its peers into a graph that maps each data key to a
peer. Such structured P2P systems use the Distributed Hash Tables as a
substructure where data objects either values or location information is
placed.
Unstructured
P2P:
In unstructured overlay networks the overlay network
organize peers in a random graph in flat or hierarchical manner and uses
flooding or random traversing or expanding Time-To-Live search on the graph to
query content stored on overlay networks.
Distributed
Hash Tables:
Current widely-used P2P networks rely on central
directory servers or massive message flooding, clearly not scalable solutions.
Distributed Hash Tables (DHT) are expected to eliminate flooding and central
servers, but can require many long-haul message deliveries.
Although many theoretical schemes for minimizing routing
information have been proposed and many designs for DHTs have recently become
prominent discussion topics, we are unaware of any practical and efficient
system combining both.
Latest
Research in P2P:
In order to get the latest that is happening in this area
I decided to get some latest research papers online and went through them.
According to my limited research that I did on this topic I found out that the
over lay under lay mapping is very important in this domain of network models. The
nodes that are that are connected logically should be close to each other
physically as well in order to avoid network congestions and other delays.
Following is a brief summary of the latest research being
carried out.
EGOIST Overlay Routing
using Selfish Neighbor Selection
This paper discusses the
issue of connectivity management, folding new arrivals into an existing
overlay. Work has been done on this matter before dealing with devising
practical heuristics for specific applications designed to work well in real
deployments, and providing abstractions for the underlying problem that are
analytically tractable, especially via game-theoretic analysis. The authors of
this paper have combined these two approaches and came up with a distributed
overlay routing system called “Egoist”. Connectivity management is called upon
when having to wire a newcomer into the existing mesh of nodes (bootstrapping),
or when having to rewire the links be- tween overlay nodes to deal with churn
and changing network conditions. Connectivity management is particularly
challenging for overlay networks because over- lays often consist of nodes that
are distributed across multiple administrative domains, in which auditing or
enforcing global behavior can be difficult or impossible.
In a typical overlay network, a node must
select a fixed number (k) of immediate overlay neighbors for routing traffic or
queries for files. To solve this, the authors tried and tested the selfish
neighbor selection technique which was different from traditional techniques.
DHTs are able to provide the best possible indexing of objects in a network. On
the other hand, routing of traffic on DHTs has been shown to be sub-optimal due
to local forwarding [17, 24]. Egoist can be integrated as a different layer in
DHTs; when an object is mapped onto a node, Egoist is responsible to optimally
route the content. In Egoist, a newcomer overlay node vi connects to the system
by querying a bootstrap node, from which it receives a list of potential
overlay neighbors. The new- comer connects to at least one of these nodes,
enabling it to participate in the link-state routing protocol running at the
overlay layer. As a result, after some time, vi obtains the full residual graph
G−i of the overlay. By running all-pairs shortest path algorithm on G−i, using
Dijkstra’s algorithm, the newcomer is able to obtain the pair-wise distance
(delay) function dG−i . In addition to this information, the newcomer estimates
dij , the weight of a potential direct overlay link from it- self to node vj ,
for all vj ∈ V−i. Using the values of dij and dG−i , the newcomer connects to
G−i using one of a number of wiring policies. Each node listens to all the
control messages of the link state protocol and propagates them only to its
immediate neighbors. In order to reduce system’s control traffic, each node
propagates only unique messages by dropping messages that have been received
more than once or have been superseded. In Egoist, a node selects its neighbor
based on best response strategy. They also employed fast approximation versions
based on local search instead of long arithmetic computation which will not
only reduce computational cost but also enhance scalability. Egoist’s BR
neighbor
selection
strategy assumes that existing nodes never leave the overlay. Therefore, even
in an extreme case in which some nodes are reachable through only a unique
path, a node can count on this path always being in place. This can be a one
set back of this technique. Egoist also deals with the cheating nodes (using
the system to route one’s own traffic but denying routing to any incoming
traffic from other nodes) very efficiently in which the nodes periodically
select a random subset of remote nodes and “audit them” by querying the
coordinate system for the delays of the outgoing links of the audited nodes and
comparing them to the actual values that the audited nodes declare on the
link-state routing protocol.
Delays are
natural cost metrics for many applications, especially those involving
interactive communication. To obtain the delay cost metric, a node needs to
obtain estimates for its own delay to potential neighbors, and for the delay
between pairs of overlay nodes already in the network. Using ping, one-way
delay is estimated to be one half of the measured ping round-trip-times (RTT)
averaged over enough samples. The performance of the system was measured on the
basis of different cost metrics such as link and path delays, node load and
available bandwidth. Results of the experiments are represented graphically
which showed a positive outcome and the system out performed similar previous
work done relating to this. They’ve also made it available for use for any
third party application through their API. This way, both the application and
its Egoist node run at the same node.
This was a very comprehensive paper about the work that
authors of this paper carried out. All the basic working, idea behind it and
the results were shown in detail explaining every aspect if the new system that
they’ve designed. This work definitely have a lot of real world application as
the one they’ve explained (Multiplayer P2P gaming) which makes it an extremely
appealing and the best strong point of this paper.
Other Hot Areas:
·
Improving Unstructured Peer-to-Peer Systems by Adaptive Connection
Establishment
· Improving
the Interaction between Overlay Routing and Traffic Engineering
·
ISP-Friendly
Live P2P Streaming
·
Scalable
Resilient Overlay Networks Using Destination-Guided Detouring









0 comments:
Post a Comment